Digital Content Has a Dark Side… Is Blockchain the Solution?
More than 5-billion people are texting, tweeting and blogging in today’s hyperconnected world, which has created over 2.7-zettabytes of digital content. Over 571 new websites are created every minute of the day and 30-billion pieces of content shared on Facebook every month. Big Data indeed, but digital content has a dark side. In a hyperconnected world, access to this data isn’t restricted, everyone has access.
Unfortunately, the combination of digital networks and traditional data structures has unwittingly spawned an acceleration of hacking and fraud. It is arguable that no data system constructed today, using traditional IT architecture, is safe from a determined hacker. As we stand on the threshold of the next wave of the digital revolution with the emergence of the Internet of Things (IoT), this digital content vulnerability could become more than problematic unless we transform the basic architecture for how we build IT systems. This is where a new technology, blockchain, could make a big difference.
As defined on BlockchainTechnologies - "Blockchain is a type of distributed ledger, comprised of unchangeable, digitally recorded data in packages called blocks (rather like collating them on to a single sheet of paper). Each block is then ‘chained’ to the next block, using a cryptographic signature. This allows block chains to be used like a ledger, which can be shared and accessed by anyone with the appropriate permissions."
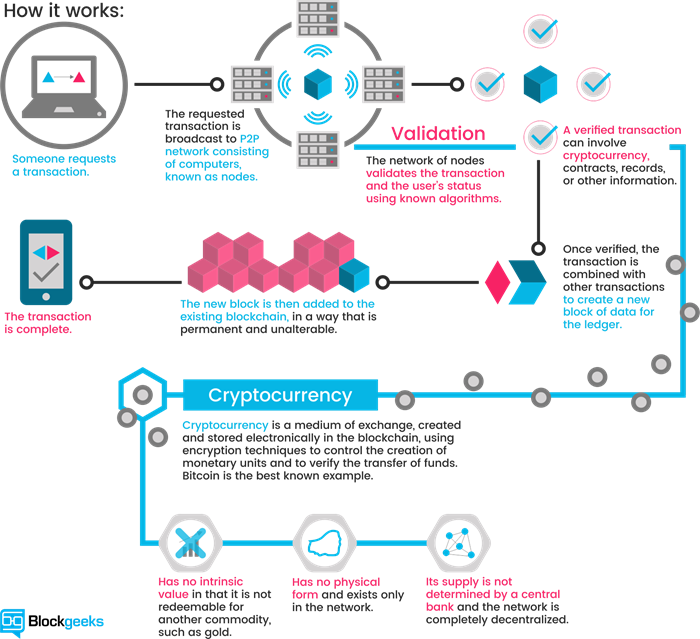
To understand blockchain technology in layman terms we will use the old campfire activity. A growing story that nobody knows the end of, or even if it will end.
The objective is to create a story, with everyone adding their parts, in turn. Someone starts the story by saying a few lines, and ending mid-sentence, just before some action happens. The next person repeats what the first persons said and has to finish that sentence with something that makes sense, and then continues the story, using their own idea, since they don't know what the first person was thinking. The cycle is repeated adding more lines to the story. It continues in a similar fashion with each person repeating the whole story from the beginning, adding a couple lines, and ending mid-sentence. At some point, the "next" person will not be able to repeat, even in their own words, the story so far, and the chain fails, hence ending. Once everyone has had a chance to participate, you can pick up the chain and finish the sentence, and the story, bringing it to a successful completion.
After the story, or stories, have run their course, you can relate the process to a blockchain. Each piece (except the first) depends upon the preceding piece and is meaningless without it. If, at any point, someone in the chain doesn't hold up their part of the "contract," by completing the previous sentence, the story is ruined. Still, even without an end, everything up to the last incomplete sentence remains valid and can be traced back to the original piece.
The stored information in a blockchain is both transparent and private, which makes it a perfect architecture for the IoT. This is accomplished by separating identity verification from transaction validation. Thus, all the attributes of a particular person can be known without knowing his or her identity. This is possible because blockchain employs avatars as an information processing mechanism to preserve individual privacy.
When we look closely at how blockchain works, we discover that it processes information very differently from traditional IT systems, which are essentially hierarchical structures. Accordingly, data are organized into centralized files and use control mechanisms to accomplish work and maintain security. Blockchain systems, however, are networked structures that record information in distributed storage and use consensus dynamics to do work and maintain security.
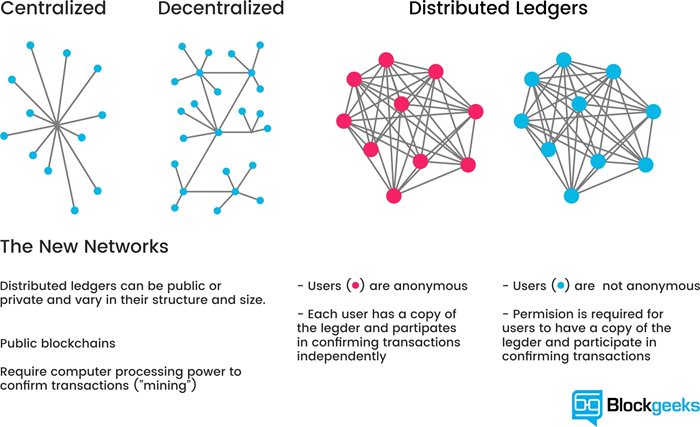
Before the internet, hierarchical architecture worked reasonably well because it was very difficult for bad guys to access proprietary mainframe IT systems. But that changed when the internet transformed the digital landscape into a hyperconnected world, making traditionally built systems vulnerable to security breaches. Once an intruder is in the system, he can easily access the centralized files, rewrite code, unilaterally commit fraud, or wreak general havoc. Because blockchain doesn’t use centralized files, if intruders find their way into the system, the distributed data is unintelligible. They are prevented from doing harm because they can’t affect any action in the system without a consensus of the blockchain network.
Blockchain has extended its reach beyond the alternative payment system behind token currencies like Bitcoin and in a world in which people are becoming increasingly concerned about the safety of their digital content. This systems architecture is likely to revolutionize the way we build IT systems. Blockchain just might be the right solution.

Natalie Evans
Natalie Evans has over 16-years in the tech industry and currently works as the event coordinator and tech reporter for CMS-Connected, keeping up-to-date on what's happening in and around the Content Management industry.